Proactive, comprehensive protection for your critical assets. Focus on growth with continuous monitoring, threat intelligence, & rapid response. Guaranteed peace of mind.

Uvation Managed Security offers comprehensive protection for digital assets, initiatives, and growth, bringing peace of mind against cyber threats. Proactive intelligence and monitoring mitigate risks pre-impact, ensuring uninterrupted operations. This includes real-time endpoint security against sophisticated attacks.
Gain strategic compliance & cost-effective security with Uvation. Easily meet regulatory requirements, avoiding penalties & damage. Outsourcing significantly cuts costs of in-house experts & infrastructure, providing scalable, top-tier protection aligned with your budget.
Ensure business continuity with Uvation's rapid incident response. Our team quickly neutralizes threats, minimizing impact and downtime. Continuous 24/7 monitoring provides round-the-clock surveillance, swiftly identifying & addressing issues to maintain peak digital asset security.
Uvation’s Managed Security Operations begin with a comprehensive Security Risk Assessment of your current posture. Our experts identify vulnerabilities and recommend mitigation measures, laying a solid foundation for your security strategy. This evaluation is crucial to safeguarding your digital assets against evolving cyber threats, ensuring peace of mind and continuous safety for your business.
Uvation’s Managed Security provides Advanced Endpoint Protection, securing every endpoint across your organization from sophisticated attacks. Our solutions offer real-time monitoring and protection for devices, ensuring they remain shielded from malware and other cyber threats. This safeguards your digital assets and critical data from evolving risks.
Uvation offers Proactive Network Security Management to protect your network infrastructure with advanced security solutions. We deploy firewalls, intrusion detection systems, and other technologies to safeguard your data flow, ensuring its integrity and confidentiality. This proactive approach protects your mission-critical data.
Uvation provides Continuous Security Monitoring with a dedicated team offering round-the-clock surveillance of your systems & data. We monitor for unusual activity and ensure threats are identified & addressed swiftly, maintaining the highest level of security for your digital assets. This ensures proactive threat intelligence and rapid incident response.
Uvation invites you to a personalised demo of our Managed Security Operations, tailored for your business.
Our experts will guide you through comprehensive capabilities to safeguard your digital assets against evolving cyber threats, ensuring continuous protection.
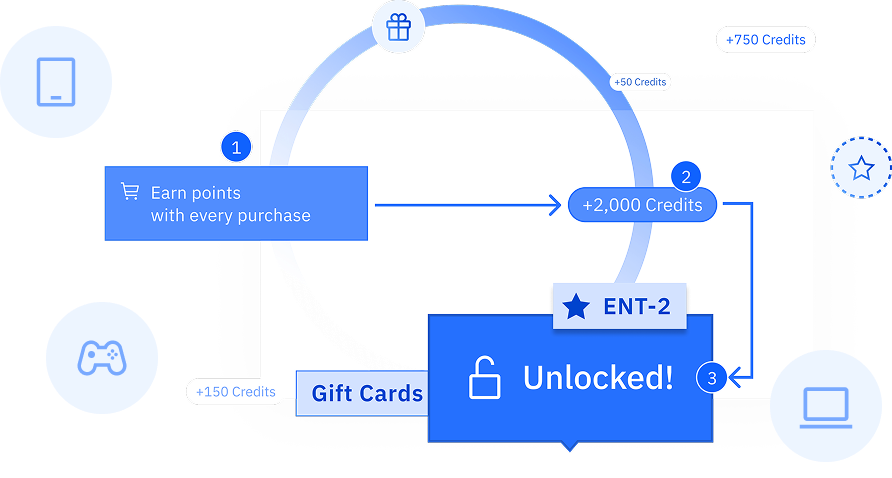
Each demo qualifies you for a $2,000 Uvation Service Platform credit and a $50 gift card.

What are our clients saying about Uvation.
A Security Risk Assessment evaluates vulnerabilities, exposure points, and security posture across systems, users, infrastructure, and policies. It typically includes asset inventory, vulnerability scanning, compliance mapping, detailed reporting, and prioritized remediation planning so leadership understands threats and the actions required to reduce risk.
Risk assessments are recommended annually at minimum, but quarterly or event-triggered reviews (new infrastructure, compliance requirements, mergers, or cyber incidents) provide stronger protection—especially for rapidly evolving or sensitive environments.
Yes. The assessment includes a clear remediation roadmap that outlines priorities, timeframes, responsible teams, and cost considerations so organizations can act on findings rather than simply receive a report.
Endpoint protection includes antivirus, EDR/XDR, patch management, device policy enforcement, zero-trust access controls, ransomware prevention, and automated threat response. Protection extends across desktops, mobile devices, cloud workloads, and remote users.
Modern endpoint solutions are engineered for minimal overhead and optimized resource usage. Security enforcement happens intelligently and often at the cloud level, so users remain fully productive without noticeable slowdowns.
Remote and hybrid workers are fully supported through cloud-based endpoint management, real-time policy enforcement, secure remote access, and automated compliance checks—even when devices never connect to the internal network.
It includes firewall configuration, IDS/IPS tuning, traffic visibility, segmentation, access control policies, VPN governance, and security policy enforcement. The goal is to ensure networks are continuously hardened and aligned to compliance and operational requirements.
Yes. Controls and reporting can be aligned to SOC 2, ISO 27001, HIPAA, GDPR, PCI-DSS, and government or industry-specific regulations to simplify audits and maintain ongoing compliance.
Continuous monitoring involves real-time detection of security events, log analysis, behavioral tracking, SIEM/SOAR automation, threat intelligence updates, and proactive incident response. This reduces dwell time and increases visibility across users, workloads, networks, and cloud environments.
Yes. Response levels vary based on the service tier but typically include triage, threat containment, root-cause analysis, and post-incident reporting to prevent recurrence.
Threat detection is powered by AI-enhanced analytics, threat intelligence feeds, and analyst validation within a 24/7 security operations center (SOC). This reduces alert noise and ensures only relevant events require escalation.
Yes. The service supports integration with existing SIEM, EDR, identity platforms, firewalls, and third-party solutions to maximize current investments and avoid operational disruption.
Response time depends on the SLA tier, but typical engagement ranges from immediate automated response to analyst-led intervention within minutes. The objective is rapid isolation, containment, and remediation.
Reports are delivered through dashboards, monthly compliance summaries, quarterly strategic reviews, and executive briefings tailored to both technical and non-technical stakeholders.
Organizations typically experience higher security maturity, faster compliance readiness, reduced operational risk, improved threat response time, and greater visibility into their organization’s security posture—all while reducing internal resource burden.
Enjoy exclusive benefits like loyalty points, service platform credits, and gift card opportunities with each purchase you make at Uvation. Our rewards program makes choosing Uvation the smarter decision.
Learn more about our Rewards