
Writing About AI
Uvation
Reen Singh is an engineer and a technologist with a diverse background spanning software, hardware, aerospace, defense, and cybersecurity. As CTO at Uvation, he leverages his extensive experience to lead the company’s technological innovation and development.

Traditional cybersecurity methods—such as network firewalls, IAM policies, and encryption at rest—are insufficient for modern AI-first environments. AI models are considered valuable Intellectual Property (IP), meaning their weights, prompts, and training data must be protected as business secrets. Furthermore, training involves highly sensitive data in regulated sectors like healthcare and finance. Since AI is not static and continuously evolves through fine-tuning and user feedback, it introduces fresh and persistent attack surfaces that perimeter defenses cannot adequately cover. This context demands a new AI security strategy focused on integrity, privacy, and regulatory readiness.
Confidential Computing is a paradigm that moves security beyond perimeter defenses, embedding trust directly into the silicon hardware. It secures data in use—not just at rest or in transit—by running AI workloads within Trusted Execution Environments (TEEs). TEEs are hardware-isolated areas within a CPU or GPU where data and code remain protected, even from the host operating system or the cloud provider. This capability grants AI workloads essential protections, including encrypted memory and processing, tamper-proof model execution, and remote attestation to verify runtime integrity. This approach strengthens compliance with crucial standards like HIPAA, GDPR, and ISO/IEC 27001.
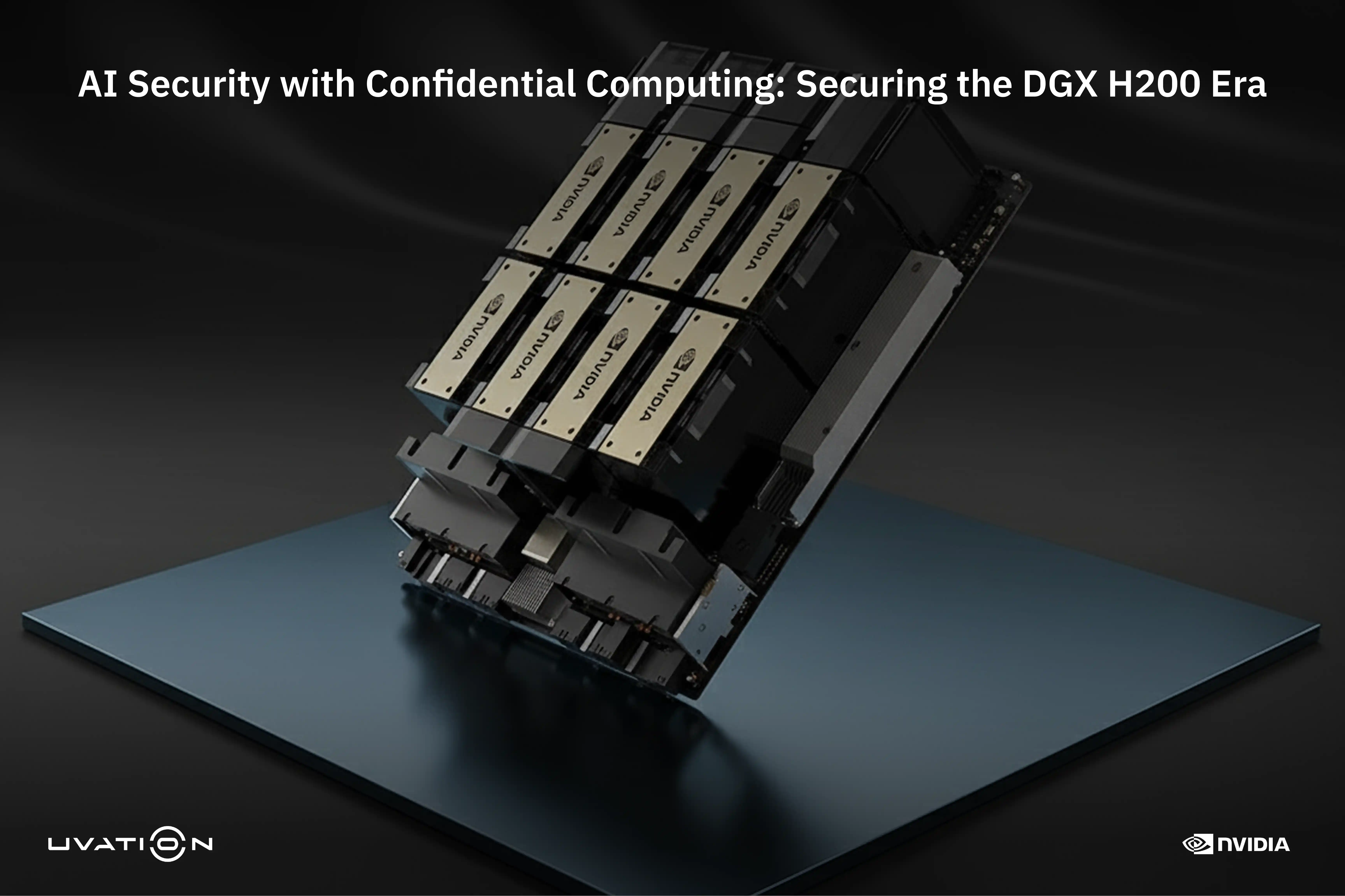
The NVIDIA DGX H200 is designed as a trust anchor, enabling AI security at the hardware-software boundary. Crucially, the platform wraps the H200 GPU’s immense 141 GB of HBM3e memory—perfect for large language models (LLMs)—with essential hardware protection. This protection includes firmware attestation, secure boot chains, and hardware root-of-trust. Even when deploying billion-parameter models, the data and logic remain protected from side-channel leaks or host intrusion. This is enabled by integrating the NVIDIA Confidential Computing Architecture, which features GPU Confidential Containers, Enclave-Enabled Runtimes (like PyTorch + Triton), and Remote Attestation APIs.
The combination of Confidential Computing and the DGX H200 directly defends against several non-hypothetical threats. For instance, it prevents Model Theft by running models within encrypted memory where the host has zero visibility. It defends against Prompt Injection attacks against hosted LLMs by validating the input chain integrity via enclave validation. Hardware isolation prevents memory sniffing and timing leaks, thereby mitigating Side-Channel Attacks. Furthermore, attestation ensures verified code and dataset integrity, preventing the deployment of Poisoned fine-tuning datasets. The secure architecture also allows organizations to safely run complex workflows like secure federated learning and inference across untrusted edges or multi-tenant platforms.
The DGX H200 architecture is specifically designed to eliminate the historical trade-off between security and performance. The integration of confidential computing technologies ensures end-to-end protected AI without sacrificing speed. Secure, high-speed communication between GPUs is maintained through NVLink 4.0 and the NVSwitch fabric. The system also utilizes FP8 and TF32 support, which enables privacy-preserving AI while reducing compute overhead. Additionally, runtime control is integrated via tools like Triton Inference Server and NVIDIA NeMo Guardrails without causing latency spikes. The DGX H200 is proof that powerful performance and protection can coexist.
Enterprises seeking to build production-grade secure AI systems must adopt a structured approach. This deployment stack begins with Secure Infrastructure Blueprinting to establish the root-of-trust hardware design. Next is Confidential AI Integration, which involves setting up NVIDIA Confidential Containers and configuring secure enclaves. Essential to maintaining trust are Attestation Workflows—scripts for remote verification across cloud, edge, and on-prem deployments. Finally, implementing a Governance Layer ensures the entire system aligns with compliance frameworks such as ISO 27001, NIST CSF, and other sector-specific norms.
We are writing frequenly. Don’t miss that.

Unregistered User
It seems you are not registered on this platform. Sign up in order to submit a comment.
Sign up now