
Zero-Trust Security Implementation: How Managed Services Turn Strategy into Continuous Protection
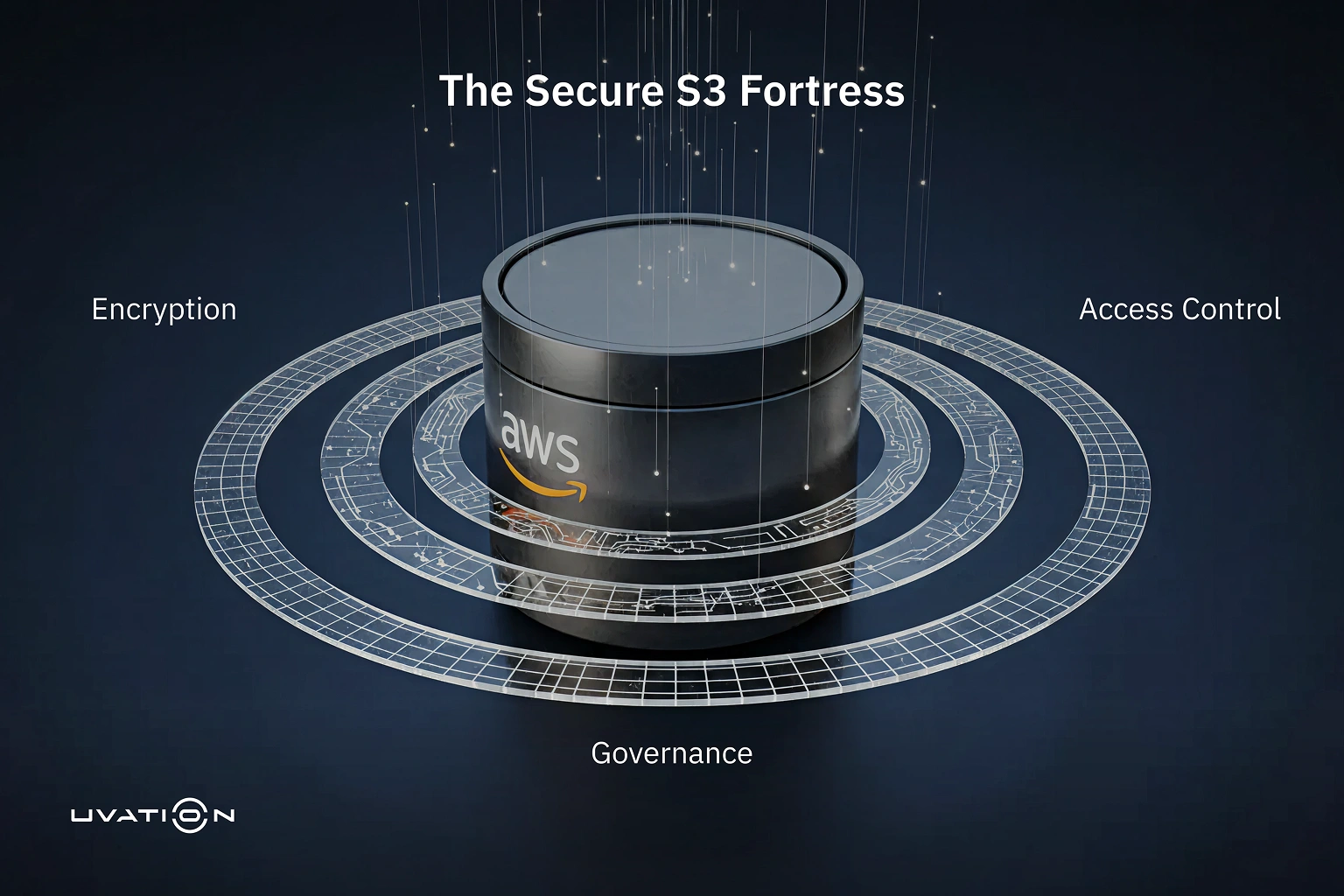
Zero-trust security replaces obsolete perimeter defenses with a model that assumes breach and mandates explicit verification for every access request, regardless of location,,. Unlike static deployments, zero trust is an operating discipline reliant on identity-centric controls, least-privileged access, and continuous validation,. However, implementations often fail due to operational complexity, alert fatigue, and fragmented visibility,,. To sustain protection, organizations require continuous execution rather than just initial design. Managed security operations bridge this gap by providing the necessary 24×7 monitoring and incident response to validate access decisions and detect identity-based threats in real-time,. Ultimately, success is measured by reduced lateral movement and sustained data loss protection, transforming zero trust from a strategy into lasting operational resilience,.
14 minute read
•Technology










Unregistered User
It seems you are not registered on this platform. Sign up in order to submit a comment.
Sign up now